After initially blaming an “unplanned system outage” for its computer networks being knocked offline since early Monday, Apex Capital Corp. and its subsidiary, TCS Fuel, confirmed that both companies’ systems were targeted in a malware attack.
Ransomware gang BlackByte is claiming responsibility for infecting the operating systems of one of the largest factoring companies in the U.S., Apex Capital, headquartered in Fort Worth, Texas, which, in turn, shut down TCS Fuel’s network.
In February, the FBI and the U.S. Secret Service (USSS) released a joint Cybersecurity Advisory (CSA) about BlackByte. The report described the gang as “a Ransomware-as-a-Service group that encrypts files on compromised Windows host systems, including physical and virtual servers.”
Some small-business truckers who utilize Apex Capital to factor their accounts receivable or fuel their trucks using discount fuel cards through TCS told FreightWaves they were alarmed Monday morning when they were unable to log on to the companies’ systems, fuel their trucks or access funds to pay their owner-operators.
Apex Capital and TCS Fuel specialize in providing financial services for small and medium-size trucking companies.
Sherry Leigh, chief product and marketing officer at Apex, reiterated to FreightWaves and its customers that the company “remains financially strong.”
“We were infected by malware, and we are continuing to work around the clock to get our systems back online,” Leigh said in an email. “The good news is our core systems and client databases remain intact and we are successfully bringing our processing back online. However, this continues to be a slow process.”
On Tuesday, Leigh declined to comment about what data may have been stolen by the hackers who accessed Apex’s system.
Late Wednesday, Chris Bozek, president of Apex Capital Corp., posted a message on the company’s website and social media accounts, including Twitter, about its efforts to fund its trucking customers.
“Our employees continue to work diligently to process invoices and fund our clients,” Bozek said in the statement. “Despite these trying circumstances we are doing our best to provide you the best service possible.”
Brett Callow, threat analyst at Emsisoft, confirmed that BlackByte was responsible for the ransomware attack on Apex Capital and is using evolving methods to target its victims.
“You’ll see they’ve got some new tactics,” Callow told FreightWaves. “Victims can pay to extend the time until the [confidential] data is published, to have the data deleted (supposedly), while anyone can pay to download it.”
According to BlackByte’s ransomware demand, anyone can pay $5,000 to extend the company’s data release for 24 hours, $300,000 to destroy all the information and $200,000 to download all of Apex’s data. Soufiane Tahiri, an information security engineer, shared details about the malware attack on his Twitter account early Wednesday.
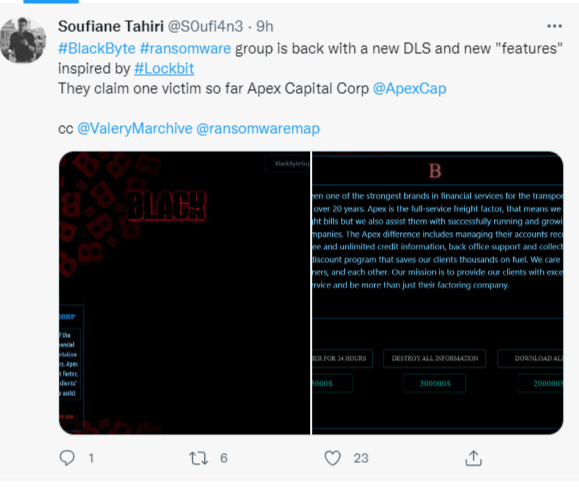
“The price [to download the data] could be set intentionally low,” Callow said. “The hackers may hope that the victims will believe the low price will result in one or more third parties buying it should they not pay the demand to have the data (supposedly) taken off the market. The third parties in question could be other cybercriminals or perhaps even competitors [of Apex].”
Callow said it’s unclear where BlackByte’s operation is based but added that it’s possible there’s some overlap with another ransomware operation: Conti.
“Also, the fact the developers may be based in a particular country or countries doesn’t mean that it’s where the attack came from. The groups effectively “rent” their ransomware to affiliates who use it in their attacks — and the affiliates can be based anywhere,” he said.
Bozek said Apex is working around the clock to get “our systems back up and running again.”
This is a developing story.
Do you have a story to share? Send me an email here. Your name will not be used without your permission in a follow-up article.








Lewis
I highly recommend this fair service. Wizard James Recovery Service did a fantastic job at recovering my life savings which got stolen. I had a stressful situations going on and they were so patient with me and did help me through this. The staff members seemed legit, not just classifying the problem and charging not without good response. I must commend them for recovering my money from the people who stole from me. If you are ever in need of such service, you can contact them via: wizardjames8@yahoo.com or WhatsApp: +1 (863) 254-2842
Frank
Hello Netizens, I was able to win my divorce case against my wife with the help of a friend who referred me to Dr Joel, who assisted me in hacking through my wife’s Email, Chat, SMS and expose her for a cheater she is. I just want to say a big thank you to Dr Joel, i am sure someone out there might be going through my experience, reach Dr Joel on (dr.joelvey44naths at gmail dot com) OR Whatsvpp (+1-252-512-0391) so you don’t pay unnecessary alimony.
Frank
Hello Netizens, I was able to win my divorce case against my wife with the help of a friend who referred me to Dr Joel, who assisted me in hacking through my wife’s Email, Chat, SMS and expose her for a cheater she is. I just want to say a big thank you to Dr Joel, i am sure someone out there might be going through my experience, reach Dr Joel on (dr.joelvey44naths@gmail.com) OR WhatsApp (+1-252-512-0391) so you don’t pay unnecessary alimony.
ANITA
I know and can recommend a very efficient and trustworthy hacker. I got his email address on Quora , he is a very nice and he has helped me a couple of times even helped clear some discrepancies in my account at a very affordable price. he offers a top notch service and I am really glad I contacted him. He’s the right person you need to talk to if you want to retrieve your deleted/old texts,call logs,emails,photos and also hack any of your spouse’s social network account facebook,instagram,telegram, tiktok,messenger chat,snapchat and whatsapp, He offers a legit and wide range of hacking services. His charges are affordable and reliable, This is my way of showing appreciation for a job well done. contact him for help via address below..
Email : intertechhacker264@gmail com
ANITA MCKAY
Get into your spouses and kids phones and other gadgets without them knowing or suspecting. It feels good and safe to know what your family members and loved one’s does at always without them knowing . I had always thought it was never possible to monitor your partner or children without them noticing, but all thanks to him I am able to view my partners activities without her even knowing Write to :intertechhacker264@gmail com
Patricia Thomas
Small business already hit hard and now cannot even move their trucks. How can we actually trust any of these companies to be safe enough to give us peace of mind to know that we can take care of our families.
noora
Makes 💵$340 to 💵$680 per daydf online work and I received 💵$21894 in one month online acting from home. I am a daily student and work simply one to a pair of hours in my spare time. Everybody will do that job and online ask extra cash by simply
copy and open this site .…………> 𝐰𝐰𝐰.𝐬𝐚𝐥𝐚𝐫𝐲𝐛𝐚𝐚𝐫.𝐜𝐨𝐦
Dave
Interesting choice of words for the headline. “Blames” implies there’s still doubt about what actually happened. That’s not the case here.
Shelby z
Probably because you were not transparent with the fact that it was not a system outage but rather a ransomware attack . These clients should all change their banking info ASAP as these hackers now have ALL of these poor peoples private information, and who knows what they will do with it