Nothing can prevent attacks which can cripple businesses for weeks, but simply steps do help
If it seems as though cyberattacks are becoming more commonplace, it’s because they are. The Ponemon Institute’s 2015 Cost of Cyber Crime report noted that cyber crime cost affected companies an average of $6.5 million in 2010, but had doubled to nearly $13 million by 2015. The maximum cost in 2015 was $65 million. That year, there were an average of 160 successful cyberattacks per week, up from just 50 per week in 2010.
According to Panda Labs, in 2016, there were 18 million known malware samples found in the third quarter alone. The Computer Crime and Intellectual Property Section (CCIPS) says there were more than 4,000 ransomware attacks per day in 2016, a 300% increase over 2015. Security firm Symantec reports that one in 131 emails sent in 2016 contained malware, the highest rate in five years. And business email compromise (BEC) scams, relying on spear-phishing emails, targeted over 400 businesses every day, draining $3 billion over the last three years, it said.
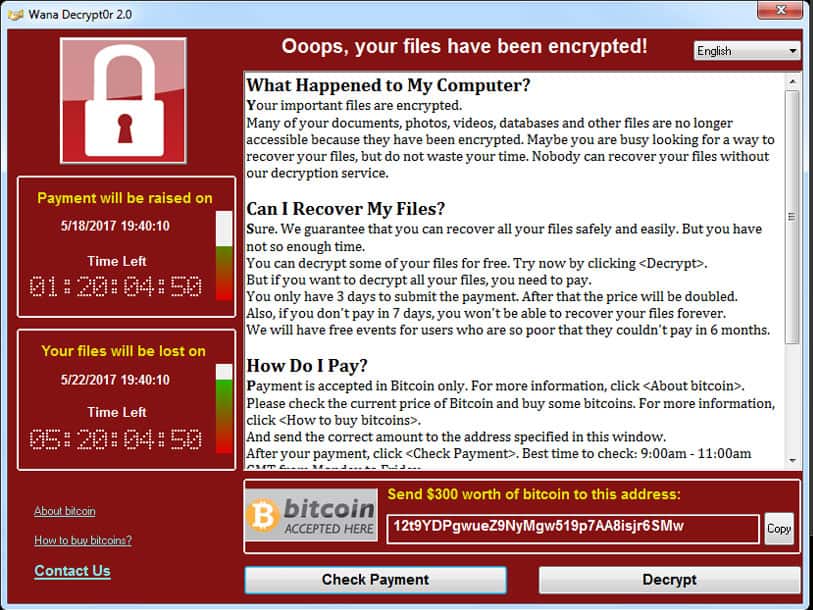
The numbers are staggering. The late June Petya ransomware attack, dubbed GoldenEye, hit several shipping companies hard, including FedEX-owned TNT Express and global shipping firm Maersk. It followed the WannaCry attack in May that effected more than 200,000 computers in 150 countries.
As of Monday, nearly a week after the attack, TNT was still trying to recover. The company makes more than 1 million deliveries per day in 61 countries; many of those deliveries have been delayed. The impact to TNT Express caused FedEx to issue guidance to investors.
“We cannot measure the financial impact of this service disruption at this time, but it could be material,” FedEx advised.
Maersk was also significantly impacted, with operations at several port terminals shut down due to the attack. Maersk owns port operator APM Terminals, which has operations on both coasts of the U.S. The company was only able to restore full operations on Monday. “Today we can finally reopen our key applications,” Maersk said in a statement. “We can, with great certainty, say that we have never experienced anything like this and therefore we are extremely excited to have achieved a milestone in the journey to be back fully online.”
Clearly, cyberattacks including ransomware are on the rise, and that means businesses big and small need to have proper defenses in place. Ransomware attacks are particularly troubling as the virus takes over the computer or computer system and won’t release it until a ransom is paid, usually done in bitcoin or some other cryptocurrency. The ransom is often small – $300, for instance – and most companies just pay the ransom hoping to get access to their computers and data again. Unfortunately, more often than not, the ransom is paid and the held computer is never released.
But with so many millions at stake, supply chain companies face a dilemma: either invest big money in online security systems – which the recent attacks show may still not be good enough – or take your chances that a cyberattack won’t happen to you.
“Shut downs of operating systems are complete handicaps for logistics companies and can cost significant amounts of lost business as well as lost productivity as assets and people are idle for a day or more waiting for critical systems to be checked and brought back online, not to mention the collateral costs for companies whose shipments are delayed,” Jason Kuehn, vice president at global management consulting firm Oliver Wyman, told FreightWaves. “If computer systems disruptions happen repeatedly, shippers will take their business elsewhere where system security and reliability are higher. Customers also worry that their confidential data may get compromised from hacking attacks on a logistics provider’s system.”
Keuhn notes that as society becomes more interconnected, such as with smart highways and autonomous vehicles, there is growing concern about infrastructure being hacked.
“There is a future concern about automated vehicles and machinery getting disrupted as happened in this last attack to radiation detectors at Chernobyl,” he says. “This will be a real concern, and I know the developers of such systems are keenly aware of this issue and are working diligently to produce automation systems that are as robust and secure as possible.”
“Shut downs of operating systems are complete handicaps for logistics companies and can cost significant amounts of lost business as well as lost productivity as assets and people are idle for a day or more waiting for critical systems to be checked and brought back online.”
For many companies, especially those in the transportation space that face small margins, investing in more secure systems presents a risk analysis – i.e., how much will it cost me to invest in online security vs. how much will it cost me if I don’t? For many firms, the answer ends up being the latter. But Keuhn says there are low-cost solutions companies can take that, while they may not prevent an attack, can help.
“One of the best low-cost steps a business can take is to keep their operating systems updated with the latest patches from Microsoft and other vendors and to have virus protection systems in place,” he advises. “It is also important to keep a back-up of their system and critical data on an offline server so that if your system is hacked, you can wipe the impacted computer(s) and restore the programs and data from the backup system.”
Like many experts, Keuhn is doubtful that paying a ransom is worthwhile.
“Everything I have read says that paying the ransom on a ransomware attack is a dubious proposition at best,” he says. “First, it encourages the attackers by rewarding them. Secondly, in many cases your computer will not be restored by the attacker as they are fearful that further contact may lead to tracing the attack back to the source.”
Keuhn also says companies should install good firewalls to thwart hackers and use and maintain an updated anti-virus checking system from a reputable company to screen files and e-mails. Also maintain all backup data and systems on an offline server so you can restore your system quickly with minimal lost data.
Many cyberattacks originate with emails, so Keuhn says to exercise extreme caution when opening emails and keep employees up-to-date on what current phishing attacks look like. “Suspicious e-mail should never be opened and should be reported as spam and deleted,” he says. “Only open e-mail (and especially attachments) from known sources and on computers with anti-virus software.”
Finally, “if you suspect an attack or you have opened a virus laden e-mail, disconnect the computer from the network immediately to minimize the ability of the attack to spread,” Keuhn says. “Quickly notify IT and take the network down to protect as many computers and your data as possible.”
Each machine and the servers should be checked for issues before restoring the network. Any machine that is compromised should be disinfected, possibly wiped clean and reconfigured and then restored prior to reconnecting to the network.
“The problem is that in many cases, by the time you are aware of a problem, it is too late and the malware may have spread beyond the attacked computer,” Keuhn says.
You may not be able to prevent a cyberattack, but there are steps any company can take to minimize the risk and possible damage.







